
Keywords:
Hacking, consumption, hackintosh, “consumerization”, Practice theory
Paolo Magaudda
1. Introduction
Until recently, the hacking of technologies, computers and devices has remained largely confined to very specific sectors of society, which mainly consisted of computer experts, software developers and tech activists. In this article it is argued that, in the last few years, hacking practices consisting in the modification and subversion of digital devices are undergoing a process of popularization, and hacking-related cultural references and discourses are growing in terms of visibility among new segments of the population, including not only software experts and computer “geeks”, but also amateurs, laypersons and non-experts.
More specifically, I suggest that hacking practices and discourses are becoming increasingly visible and widespread in society, and that this also implies some sort of change in the contents and forms of circulation of hacking discourses and practices. This change can be regarded as a “consumerization” of hacking practices, a process by which hacking objects, skills and cultures are increasingly influenced by cultural elements and discursive strategies belonging to the realm of consumer culture and practices.
For this purpose, the article focuses on the development of the “Hackintosh” practice, which consists in the modification of a non-Apple computer in order to run an Apple operating system on it. This practice, which started in 2005 within the hacking context and was mainly confined to software developers, has soon evolved in different ways, becoming increasingly accessible to non-experts as well. In particular, I will focus on the creation and diffusion of the so-called “MacBook Nano”, a low-cost netbook transformed so as to run Apple software. If the first stage of the “Hackintosh” development fits well into a canonical pattern of hacking activities carried out by computer experts, the subsequent circulation of tutorials, information and skills required to make a MacBook Nano seems to show a trajectory of popularization of hacking practices, which implies both a simplification of the technical skills required to perform this practice and an overall change in the cultural codes, discourses and communication channels involved in its circulation.
After a short description of the Hackintosh project, I will analyse some of the tutorials, guides and tools involved in the creation of a MacBook Nano, by adopting a “Practice Theory” perspective (Shatzky et al., 2001; Warde, 2005; Shove and Pantzar, 2005). Besides, I will discuss how objects, skills and discourses involved in the practice of hardware modification are influenced by other cultural elements related to consumer culture.
2. Hacking, society and the modification of computer hardware
In the last fifteen years, the realm of hacking has received growing attention by social sciences, journalists and intellectuals. If in the media it is today common to find news about hacking activities, the hacking phenomenon has also been given more and more consideration by social scientists. Since the eighties, the hacker culture has actually acquired a more prominent status in society, especially after the description of the hacker ethics by tech expert Steven Levy (1984), who praised it as a libertarian culture, aimed at ensuring free access to information and a better quality of life. Years later, the hacking ethics has also been associated with the emergence of a new form of production and with a new way to manage the relationship between work and life, being regarded as the progressive evolution of what Max Weber defined as the “ethic of capitalism“ (Himanen, 2001). Among the most common discourses about the hacker culture, the distinction between “black hat” and “white hat” hackers has become a dominant interpretation of a chaotic phenomenon, making it possible to establish an ideal distinction between progressive and legal forms of hacking and dangerous and illegal cybercrimes (see Jordan, 2008).
Another relevant line of research on the hacker culture has pointed out the conflict and tension existing between the computer security industry and the “computer underground”, which clearly represents the most “institutional form” to understand the meaning of hacking (Taylor, 1999). Moreover, more recently, the discourses on the hacker culture have also been developed within a more explicit political framework, introducing the definition of “hacktivism”, which is today a common expression used to refer to the subversive use of computers to promote mainly radical political ideas and practices (Jordan 2002; Jordan and Taylor, 2004).
As it is possible to see from this very short summary, hacking has generally been regarded by scholars as something that mainly refers to, and is relevant for, the side of production and creation (of objects and discourses), and has more specifically been associated with two main social categories: software professionals and political activists. It has been very rarely considered how hacking practices are instead also increasingly meaningful for the consumption side and for the patterns of circulation of goods. Hacking practices can actually be fruitfully regarded as inextricably embedded in consumer societies, so much so that their recent evolutions could lead to redefine social boundaries, tensions and mutual influences between the production and the consumption side.
Very recently, some scholars have started to consider hacking practices in relation to consumption issues. One of these few attempts is the work of Söderberg (2008), who has developed an analysis of hacking within a Marxist framework, observing not only that hacking is deeply rooted in the very nature of consumer-capitalist society, but also that the evolution of hacking practices is questioning the capitalist traditional circulation of goods, breaking the conventional cycle of production-consumption (p. 109 et seq.). However, in his discussion of the tensions between hacking, production and consumption, Söderberg does not provide empirical evidence of the actual ways in which hacking is related to consumers’ attitudes and practices, remaining on a purely theoretical level. Another perspective is the one developed in Magaudda (2010), where it is pointed out that some of the typical features characterizing the hacking realm – such as the involvement of users in the modification of the technologies they use, or the more or less explicit political significance of the products they modify – can be seen as specific points of connection between hacking and consumption.
The lack of consideration of the relationship between hacking and consumption can be attributed to at least two separate factors. The first factor is that hacking is an activity originally developed within expert circles and professional environments. Given the roots of this phenomenon, it is not surprising that scholars have not promptly focused on the elements that hacking and consumer practices have in common, concentrating on the involvement of experts and professional users rather than on the implications for laypersons. The second factor that helps explain the lack of consideration of the consumption-hacking nexus is the general tendency of social and human sciences to privilege the analysis of production rather than that of consumption. Since Karl Marx’s analysis of the “relations of production” (Marx 1847), the investigation of social life has always been focused on production-related issues. As we have already pointed out, Max Weber (1921) recognized the basis of capitalist society in the Protestants’ commitment to work and in their attitude toward money (an interpretation refuted by Campbell, 1987, who pointed out the role of a “romantic ethic” in the understanding of capitalism and consumerism). In other words, it was not until very recently – between the seventies and the eighties of the last century – that social sciences started to reflect on their object of analysis in terms of “consumer society” (see Debord, 1967; Baudrillard 1970). The lack of recognition of the constitutive role of consumption in society has affected both the analysis of society in general and, consequently, the understanding of hacking.
Nevertheless, there are many reasons that prompt us to consider the intersection between computer and hacking practices and the world of consumption. In this regard, the history of personal computer represents a very interesting example of a consumer product originally addressed to hobbyists and amateurs. The first personal computer was indeed commercially distributed as a construction kit, as in the case of Altair 8800 (1975), which was sold by mail order, or Apple I (1976), which was only available in hobbyist shops without case and power supply (Freiberg and Swaine, 2000). Thus, if we take a look at how personal computers were initially commercially distributed among hobbyists, it will be possible to examine the relations between computers, expert skills and consumerization from a more complex and articulated perspective.
3. Hacking, “Prosumption” and Practice Theory
Hacking practices imply an active interaction with the objects we use, as well as a tendency to modify and re-adapt standard products. In the last decades, this tendency of users and consumers to modify standard products and to materially participate in the co-production of their own products seems to have acquired a relevant role in consumer culture. One of the first references to a more complex relation between consumers and their co-production of goods comes from cultural critic Alvin Toffler (1980), who coined the term “prosumer”, a conflation of “producer” and “consumer”. Following this perspective, more recently, Colin Campbell (2005) referred to the consumer’ involvement in the modification of commodities developing the concept of “craft consumer”. A “craft consumer” is someone who engages in consumer practices that imply a manipulation of commodities and is described in a way that recalls many aspects of the hacker culture. As he writes, “the craft consumer is a person who typically takes any number of mass-produced products and employs these as the ‘raw materials’ for the creation of a new ‘product’, one that is typically intended for self-consumption” (Campbell, 2005, pp. 27-28).
Another relevant question recently addressed in consumer studies is that consumers today have new powerful tools to perform their modifications of products. An increasing number of web sites, online forums and web 2.0 services provide consumers with countless opportunities to acquire the necessary skills and knowledge for manipulating commodities. The relevance of web tools for these kinds of consumption practices has recently been pointed out in a special issue of the “Journal of Consumer Culture”edited by Beer and Burrows (2010). In this issue, Ritzer and Jurgenson (2010) thoroughly examine the influence of web 2.0 services on consumer practices by developing the concept of “prosumption”, by which the two scholars refer to a wide range of practices that blur the boundaries between production and consumption, with particular regard to the use of web 2.0 applications.
One crucial point in the comparison between hacking and consumption is the complexity of the competence and skills involved in the former as opposed to the simplicity and accessibility usually associated to the latter. By adopting a Practice Theory approach to the study of ordinary consumption, Shove, Pantzar and other scholars (Shove and Pantzar 2005; Shove et al. 2007) have largely shown that ordinary consumption practices often require specific sets of skills that need to be circulated and learned. In short, Practice Theory is a theoretical framework based on the idea that, in order to better understand social phenomena, “practice” should be taken as the main unit of analysis; as a consequence, any change in individuals’ behaviours and activities should be related to the evolution of their practices and to the emerging interactions between different and previously separated practices (Warde, 2005; Sassatelli, 2007). In consumer studies, Practice Theory assumes that consumption activities are the result of individual performances imbricated and intertwined in a complex socio-material context where meanings, objects and embodied activities are arranged in specific configurations of “practices”. In this framework, the concept of “practice” is regarded as a whole, shared and stabilized “configuration” consisting “of several elements, interconnected to one another: forms of bodily activities, forms of mental activities, ‘things’ and their use, a background knowledge in the forms of understanding, know how, states of emotion and motivational knowledge” (Reckwitz, 2002, 249). These elements can pass from a practice to another, producing changes and evolutions in the practices themselves.
Following this perspective, Watson and Shove (2008) observe that the consumption practices connected with “do-it-yourself” attitudes are not only increasingly present in today’s society, but are also a crucial field for understanding the changing relationships between consumption, modification of objects and social learning of specific skills. In particular, the present article considers two relevant dimensions of the theoretical landscape of Practice Theory. First, it regards the modification of hardware as a practice involving material (the objects to be modified), cognitive (skills and knowledge) and cultural (discourses and representations) elements. Second, it points out that the evolution of hacking in society can be fruitfully explained by examining how the constitutive elements of this practice – objects, skills and discourses – are influenced by other objects, skills and discourses involved in other social practices, with particular regard to consumer culture. The cross-fertilization of hacking and consumer practices will be discussed in the conclusion of this article, after the empirical analysis.
The description which follows of the Hackintosh project and the analysis of the case of MacBook Nano are based on an online ethnographic study (Kozinets, 1998; Hine, 2000) collecting documents and notes on the subversive appropriation of technologies, with specific regard to the modification of Apple products. This ethnographic work was carried out in about six months between 2010-2011 and focuses on several forms of hackings, including the hacking of Apple’s iPhone.
4. Origins, development and circulation of the Hackintosh project
A “Hackintosh” is a personal computer based on non-Apple hardware and adapted or modified in order to run Apple’s operating system, which is known by the acronym OS X (Operating System Tenth). The name “Hackintosh” reveals the hacking origins of this object, and is a portmanteau of the words “Hack” and “Mackintosh”. The development of Hackintosh computers started with a collaborative hacking project called OSx86, launched in 2005 with the aim of developing the technical conditions for running Mac OS X on a machine based on a x86 architecture (the basic architecture of all Intel microprocessors), which Apple had adopted since 2006 in all its Macs.
At the origin of the development of the Hackintosh project there is a specific technical choice related to Apple’s commercial strategy. Since 1994, Apple computers had used a specific family of processors, the PowerPC (based on a project developed by Apple together with IBM and Motorola), but in 2005 the Cupertino company announced the decision to shift from PowerPC to Intel processors, which were deemed more efficient in terms of calculation performances and power consumption. Thus, when in 2006 Apple started to sell its Intel-based Macs together with an updated version of Mac OS X – which was originally designed to only work on PowerPC processors – it became relatively simple for experts and hackers to also run OS X “natively” (meaning without emulators or other mediating software applications) on non-Apple hardware. Moreover, it also became possible to run Microsoft operating systems on Apple computers, an option that Apple itself had exploited in commercial terms to convince new costumers to abandon their Windows-based computers in favour of new Macs able to run both Mac OS X and Windows.
Apple announced the adoption of the new processor in June 2005 and released the first generation of Intel-based Macs in January 2006. Meanwhile, just a few weeks after the 2005 announcement, the hacking community started to work on the project of running Mac OS X on non-Apple computers. The first concrete results were achieved one month after the marketing of the first Intel Mac models, and the first accredited Hackintosh computer was crafted in February 2006. This hacking project was immediately followed by a software update released by Apple to prevent Mac OS X from being installed on non-Apple hardware. From that moment on, there have been several attempts to run Apple software on non-Apple hardware, always followed by Apple’s reactions to limit or block these hacking projects, in a sort of cat-and-mouse game.
Until 2007, the hacking procedures to create a Hackintosh had however remained quite complex and difficult, requiring extensive computer skills, which made the Hackintosh only feasible for expert programmers and software professionals. In 2007, a hacker named BrazilMac (after his country of origin; see Claburn 2007) created a new simplified process for making a Hackintosh, which allowed users to easily install Mac OS X on non-Apple hardware by using a legally obtained, retail version of Apple Mac OS X. Soon afterwards, other simplified hacking techniques came to fruition, the most popular of which go by the name iATKOS, iPC and iDeneb.
One further step in the development of Hackintosh occurred when, in mid-2009, Apple released a new version of Mac OS X, number 10.6, which was named – as in Apple’s tradition – after a feline: Snow Leopard. As soon as this new version of Mac OS X was released, Russian hacker netkas created a hacking method that allowed the booting of the new Mac OS Snow Leopard on non-Apple computers. When in February 2011 Apple released the first developer preview of Mac OS X v10.7 Lion, another Russian developer, named usr-sse2, was the first who created a method to install Lion on non-Apple hardware, only 3 days after its release. This simplified process consisted in copying OS X Lion on a flash drive, and booting from it through a small program called “bootloader”.
The work carried out by hackers to install Mac OS X on non-Apple hardware has developed over the years in various ways, involving many developers as well as a number of web sites and online communities. We could rightly argue that this story does not seem very different from other previous stories involving hackers and computer “geeks”: the project was indeed started by expert programmers and developers through a collaborative online process; the continuous advances and developments in the history of this hacking project are the result of the “regular” intervention of hackers appearing, as usual, under multiple bizarre pseudonyms; the skills required to understand the processes of hacking far exceeded the abilities of even advanced amateurs and of anyone who was not directly involved in the software production process. However, as it is possible to see from this short description, the evolution of the Hackintosh project clearly evolved in the direction of a simplification of methods and procedures. These methods, originally very complex, were gradually simplified – making it possible, for example, to install a regular copy of Mac OS X or download an already patched version ready to be installed – as in the case of iDeneb, one of the most popular methods to install Mac OS X and create a Hackintosh.
This pattern of evolution is also confirmed by an analysis of the principal web sites through which the Hackintosh culture and practice have been created and diffused. The most important web sites dedicated to Hackintosh projects are actually managed by very expert individuals, mainly software developers, and are hardly understandable to the average computer user. The most important of these sites is a wiki page devoted to the development of the OSx86 project (http://wiki.osx86project.org). It contains a lot of information on how to create a Hackintosh and also collects many other resources available on other web sites. The contents of this web site – a wiki where users contribute quite chaotically to sharing information and knowledge – are still far beyond the technical skills and capabilities of laypersons.
Another relevant web site in the evolution of the Hackintosh practice is www.hackintosh.com. This site is not so much a collection of technical information coming from different sources as a set of detailed instructions and tutorials designed to help users to turn their PCs into Hackintoshes. The more practical quality of this web site is also emphasized by the short description featured on the home page, which helps the reader orientate himself or herself on the web site:
Hackintosh.com provides links to everything you need to build your own Hackintosh and get Mac OS X 10.7 Lion or Mac OS X 10.6 Snow Leopard running on an unsupported computer – Instructions, step-by-step “how to” guides, and tutorials – as well as installation videos, lists of compatible computers and parts, and communities for support. (www.hackintosh.com)
Moreover, Hackintosh.com not only provides technical tutorials, but also links together many different communities focused on various aspects of Apple hardware hacks. Like other Apple communities, the OSx86 wiki has a forum of its own (called “Insanelymac”), with discussions on how to hack a Mac. These forums can focus on specific topics of discussion, as in the case of AquaMac (http://aquamac.proboards.com), which is mainly dedicated to “modding” activities (aesthetic and functional modifications), or they can also be sub-sections of other already existing Mac communities, as in the case of Applecentral.com, a forum sponsored by “MacTech Magazine” and focused on a wide range of topics (including general topics of discussion), with only a small hacking section.
As it is common in the hacker culture, there are also technical manuals published by a variety of publishers and dedicated to Hackintosh projects. The most important is probably OSx86: Creating a Hackintosh (Baldwin, 2010), a technical guide that helps users create a Hackintosh able to run Mac OS X v10.5 (Leopard). This volume of information about the Hackintosh project is a confirmation of the interest aroused by these practices among software experts, and also shows that, in the beginning, the Hackintosh practice remained mainly restricted to those kinds of users who usually read technical software guides.
Moreover, it is worth noticing that, from a legal point of view, creating a Hackintosh raises some problems. Apple’s software is actually distributed under a specific EULA (End Users Licence Agreement), which is a contract between Apple Inc. and the purchaser. According to this EULA, Mac OS X may only be installed on Apple hardware, which makes all different uses a breach of the contract. This interpretation has also been confirmed by a U.S. Federal Court, which in 2009 ruled in favour of Apple in the “Psystar case” brought by Apple against a company who had started selling Hackintosh computers (Keizer, 2009).
5. Netbooks, hacking and the creation of MacBook Nano
At this pint of our story, the practices related to the creation of Hackintosh computers have mainly regarded hackers and software experts, using collaborative web tools. I will now focus on a sub-phenomenon of the Hackintosh project, which allows us to better focus the current process of “consumerization” of hacking practices and discourses. This phenomenon concerns the diffusion of the practice of modifying small low-budget Windows-based netbooks, which have become popular in the consumer market since 2008. I will now consider the evolution of this phenomenon to show how hacking practices have gone beyond the inner circle of computer experts. In short, this hacking practice consists in transforming a netbook into a small Mac, which can therefore be called “MacBook Nano” (see Fig. 1), a name that does not correspond to any real Apple product, but has been widely used by many tech experts and journalists (see for example Estrada, 2008; Lai, 2009).
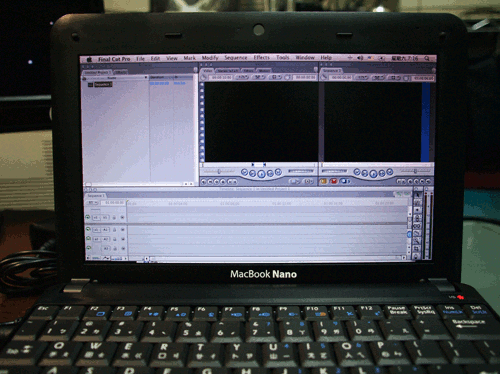
The story of MacBook Nano goes back to 2008, when a new kind of personal computer called “netbook” started to be commercially distributed on a large scale. If the initial development of the Hackintosh project was driven by a merely technical change – Apple’s transition to Intel processors – at the origin of the MacBook Nano’s phenomenon there are at least two different factors, related to the laptop market: the commercial success obtained by these new small low-price netbooks and Apple’s specific decision to stay out of this market.
One of the most crucial events in the history of personal computer was when in 2007 the PC company Asus introduced a new kind of small and inexpensive laptop computer. The new laptop had two main features: it was very small, with a screen size of 7 to10 inches and a weight of about 1 to 1.32 kilos; and it was much more affordable than a regular laptop, with a price ranging from 300 to 400 dollars. The introduction of netbooks in the market had relevant consequences on the whole portable computer sector. Between 2008 and 2010, low-cost netbooks accounted for about a fifth of the overall portable computer market (Teglet, 2009), and sales started to slow down only in 2011, after the introduction of a new category of tablet devices, (mainly the iPad (Perry, 2011). The second relevant factor that boosted the MacBook Nano’s phenomenon came from Apple. When the netbook boom started in 2008, Apple decided not to enter the low-cost product market. The position of Steve Jobs on this subject was clear, and was officially expressed to the press during Apple’s fourth quarter conference call:
I think that when people want a product of the class that we make, over and over again people have done the price comparisons and we’re actually quite competitive. So we choose to be in some segments of the market and we choose not to be in certain segments of the market. […] There are some customers which we chose not to serve. We don’t know how to make a $500 computer that’s not a piece of junk, and our DNA will not let us ship that. (Steve Jobs, October 21, 2008 – quoted in McLean, 2008)
More than two years after these declarations, Apple launched its 11-inch MacBook Air, a computer of about the same physical size as a netbook and also relatively cheaper than the average Mac laptop (but still about three times more expensive than a standard Windows-based netbook). Due to Apple’s decision not to produce a netbook-like device, Mac users were not given the chance to run Mac OS X on small laptops and could therefore not benefit from what is usually regarded, along with its aesthetic qualities, as one of the major advantages of using a Mac: its operating system.
This situation, characterized by the demand for a product that Apple had chosen not to supply, was the breeding ground for the development and diffusion of MacBook Nano. Between 2008 and 2009, while netbooks were successfully brought to the market, hacked versions of Mac OS X Leopard specifically adapted to run on these netbooks became available to users through simplified installation methods.
If, as I have already pointed out, the web sites dedicated to Hackintosh projects were only accessible to experts, professionals and “pro-amateurs”, the circulation of skills, discourses and objects related to the creation of MacBook Nano was not limited to the restricted channels generally used by experts, but involved more general web sites, adopting cultural codes and discourses different from the ones of hacker communities. In the next section, I will specifically focus on this change, which can be defined as a “consumerization” of hacking practices and culture.
6. The translation of objects, skills and discourses as a consumerization of hacking practices
As it has been said, the case of MacBook Nano had a significant impact on the development of the OSx86 hacking project, which has followed a pattern of evolution typical of the hacking context (collaborative non-profit-making projects; hackers competing with each other to be the first to hack new platforms; the use of wikis and forums, etc.). What was partially new in the case of MacBook Nano, which is also particularly interesting for the analysis of the relationship between hacking and consumption, is the emergence of a simplification and popularization of the skills, objects and discourses related to this practice.
The popularization of this practice clearly emerges from the way popular magazines and blogs have given visibility to the MacBook Nano hacking. While Hackintosh mostly evolved through wikis and forums and implied expert forms of competence and knowledge, blogs and popular magazines have instead contributed to enhancing the circulation of MacBook Nano, translating technical procedures into simpler and clearer forms. These blogs and magazines have therefore played a crucial role of intermediation between expert knowledge and laypersons’ skills, translating the complexities involved in the creation of a Hackintosh into discourses that could also be understood by non-experts.
An example of this translation process carried out by blogs is MacEee (www.maceee.blogspot.com), a blog exclusively dedicated to the installation of Apple’s Snow Leopard on a specific Asus netbook model, the EeePC 1005HA. The tutorial published in February 2010 is very simple and presents at least three specific qualities that go in the direction of a simplification of Hackintosh’s complexities. The first is that this blog only deals with one of the most popular and widespread netbook models available in 2009-2010. The procedures for the creation of a Hackintosh are therefore simplified on the basis of the needs of the users of one of the most popular netbooks on the market. The second is that the tutorial, unlike others, does not require a high level of knowledge of computer science – such as the ability of understanding and writing codes and information that appear esoteric to normal PC users. The only activities that users are called to perform are quite simple: installing the software, copying files, launching and stopping programs, checking and unchecking functions through graphical interfaces.
Finally, the last interesting element of the blog is the way the hacking procedure is discursively arranged. Even in this case, the tutorial page is addressed not exclusively to experts, but to a wider range of users. The most challenging steps of the procedure are illustrated with screen shots, and what is particularly relevant is that the tutorial – like many tool kits for laypersons (such as the Ikea tutorials) – starts with lists like “What you need” and “What is working”. The structure of this blog shows how a complex set of skills and information is popularized both with regard to the competence required and to the way the discourses are articulated, implying a process of translation of the hacking practice into the codes belonging to the realm of ordinary consumption.
Along with blogs, another crucial channel of circulation of the information related to the MacBook Nano’s modifications is constituted by the web sites of popular technology magazines, such as Wired, Gizmodo and Arstechnica. These magazines not only provide common readers with information on the advancement of Hackintosh, but also feature their own tutorials on how to make a MacBook Nano, contributing substantially to mediating specific competence and knowledge in order to make it accessible to a wider and more general readership, which mostly consists of young, highly-educated men interested in technology, but is however incomparably wider than the circle of tech experts and software professionals (for example, Gizmodo reaches 6.5 million monthly unique visitors).
One of the most popular tutorials on the creation of a MacBook Nano is the one published by Gizmodo in February and titled How To: Hackintosh a Dell Mini 9 Into the Ultimate OS X Netbook,which illustrates a hacking method for a specific and very popular netbook model, the Dell Mini 9. The tutorial is more complex than the previous one, because it also requires the use of the “terminal” (an emulator of a traditional terminal, which allows the user to interact with the computer through a command line interface). Besides, this article has a very friendly approach, compared with the general organization of knowledge of wikis and forums; it starts with a “What You’ll Need” list and provides the reader with all the relevant contextual information, including the issue of EULA violation, and with additional basic information for the general user. The article has been viewed by more than 1.2 million people (in October 2011) and, even if this figure is not indicative of the actual number of users who have carried out the modification, it clearly shows us how hacking discourses have gone far beyond the usual hacking circles.
Another relevant example of the role played by popular magazines in the popularization of MacBook Nano is an article featured on the web site of Wired magazine, which is probably the most important and authoritative source of information on science, technology and computers (co-founded by two relevant figures in the tech scene, Steward Brand and Kevin Kelly; see Turner 2008). In December 2008 Wired posted on its web site a video tutorial on how to install Mac OS X Leopard on a MSI Wind, another popular netbook (Chen, 2008). After that, Apple contacted Wired asking them to immediately remove the video, threatening to file a suit against the magazine (Buchanan, 2009). The video was promptly removed by the magazine, but Wired left a written guide on the web site with a disclaimer saying that the “process potentially violates Apple’s End User License Agreement for Mac OS X” (http://www.wired.com/gadgetlab/2008/12/gadget-lab-vide/).
The request to remove the video is also interesting because many videos on how to build a Hackintosh can be easily found on the web: in October 2011, under the name of “Hackintosh”, YouTube featured about 70,000 videos showing how to install Mac OS X on a PC. One of the most popular, viewed by more than one million users and titled How to install Mac OS X Leopard on a PC, features Tom Merritt, executive editor of CNET, another important online magazine focused on technology and gadget reviews (http://www.youtube.com/watch?v=V8oVU5AjqhU). It is not clear why Apple only asked Wired to remove the video. In any case, it was absolutely impossible for Apple to stop all the thousands of tutorials, guides and comments on the Hackintosh practice available on the web. More in general, it is possible to argue that the diffusion of successful hacking tutorials showing how to create a MacBook Nano in magazines and on YouTube was a tangible means for conveying hacking discourses and representations.
Let’s consider another case to better understand not only the increasing visibility of hacking discourses on popular online magazines, but also how the “consumerization” of hacking practices implied a change in the cultural codes and in the discourses about the objects involved in hacking practices. This case concerns one of the main tools used in the dissemination of knowledge for the creation of a MacBook Nano: namely, a “compatibility chart” that explains which netbooks are compatible with the OS X installation procedure. Before starting to create a MacBook Nano, the first step a user must take is to make sure that his/her netbook is fully compatible with the standard hacking procedures. Many web sites provide this kind of information in different forms, and, to this purpose, some of them use a compatibility chart, like the one published on Mymacnetbook.com, which represents another point of reference in the cultural mediation of the set of complex information involved in the modification practices.
On the left column, the chart presents a list of netbook models available on the market, listed in alphabetical order, and, in the horizontal top bar, the main technical components available for each netbook. At the intersection between the models and the component list, there are green, red or grey circles, which indicate whether each component will work properly after the installation of Apple software or not. Finally, on the right side of the chart, there is a direct link to the web site of U.S. Amazon, where it is possible to buy the specific model of netbook to be transformed.
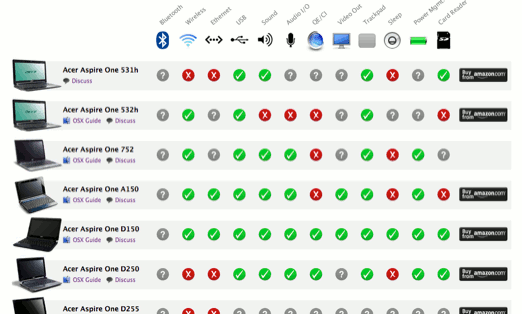
If we take a closer look at this chart, we can notice at least three interesting elements about the case of MacBook Nano, related to the process of “consumerization” of hacking cultural and discursive practices. The first element is the high degree of simplification provided by the chart, compared with the information featured on other web sites mostly addressed to experts and developers, like forums and wikis. In the chart, everything is absolutely clear even to non-expert users, who can easily understand, thanks to a simple graphical representation, if their netbooks can be transformed into a MacBook Nano.
The second element is that this simplification is obtained by adopting a specific visualization tool: a comparison chart displaying different products and all their features. Far from being typical of the hacking cultural environment, this extremely user-friendly visual chart is commonly used in consumer magazines to compare different products, as it possible to see in “Consumer Reports” in the United States, in “Which?” in the United Kingdom or in “Altroconsumo” in Italy. The organization of hacking information into a chart represents a form of semiotic translation of hacking knowledge and skills into a typical visual tool commonly used in consumer culture.
Finally, the third interesting element in the chart consists in the fact that it directly links to Amazon Store, allowing users to purchase the specific model of netbook featured in the chart. The web site providing the chart is probably part of the Amazon’s advertising program (https://affiliate-program.amazon.com/), through which it is possible to receive advertising fees from the links directed to Amazon’s online store. Clearly, this kind of advertising system, connected with the sale system of one of the biggest world technology sellers, hardly fits into the common perception of hacking ethos and practice, which is traditionally distant from big commercial companies and official business. The netbook compatibility chart therefore appears as a further element contributing to widening the circulation of hacking elements, a process marked by a cross-fertilization of elements coming from other social spheres and especially from the consumer culture and practice.
7. Conclusion: the “consumerization” of hacking practices as a cross-fertilization of different social practices
In this article I have considered the development of the Hackintosh practice and, more specifically, how a particular instance of this hacking phenomenon, the Mac Book Nano, has been spreading among a wider audience. The main point of the article is that some of the usual complexities and specificities belonging to the hacking realm have undergone a process of simplification and have partially been “translated” into a different cultural code, involving discourses and representations more traditionally associated with commercial and consumer processes rather than with computer experts’ or political hacktivists’ cultures. I have defined this tendency to simplification as a process of “consumerization” of hacking practices, showing that the entire and heterogeneous realm of hacking is today undergoing a change influenced by discourses and representations typical of the consumer culture, i.e. the cultural environment where ordinary people appropriate, consume, use and readapts products in their everyday lives. The analysis of the evolution of the practices connected with the creation of Hackintosh and MacBook Nano has drawn on a conceptual framework inspired by Practice Theory, which has allowed us to recognize how specific elements – objects, skills, discourses – typical of today’s consumer electronic culture have been readapted in relation to the practices of modification of computer hardware and software.
The relationship between elements belonging to the hacking realm and other elements associated with consumer practices can be interpreted from two opposite, but converging perspectives. The first perspective, which is the one that I have mostly focused on, allows us to interpret the MacBook Nano phenomenon as the introduction of some typical elements of consumer culture into hacking activities and knowledge. In this regard, the example of the MacBook compatibility chart clearly shows how cultural elements belonging to consumption processes can be readapted and contribute to the diffusion and sharing of the hacker culture.
However, it is also possible to point out a second form of influence, which has only implicitly emerged from our analysis of MacBook Nano: namely, the influence of hacking practices on the realm of consumer practices and on people’s attitude toward the consumption of goods. In this sense, we can see how some typical elements of the hacker culture (material modifications, function adaptations, etc.) have today become more and more usual in the ordinary consumption and appropriation of goods. In this regard, in the initial part of this article I have argued that, in consumer culture, the modification of objects are increasingly integrated into the consumption and circulation of goods (Campbell, 2005; Watson and Shove 2008). A useful example is the practice of modification of Ikea furniture, exemplified by the activities of a specific web site that symbolically makes reference to the hacking culture (www.ikeahackers.net; see Rosen and Bean 2009) and represents a possible point of connection between the hacker culture and consumer practices.
While focusing on some specific details of the practice and culture related to the Hackintosh and MacBook Nano phenomena, the article has however not explained other important issues related to the diffusion of MacBook Nano and to its uses, such as the social and technical profiles of the people involved in hacking practices, their motivations and the actual articulation of these practices. Although the documentation discussed in the article suggests that the people involved in this practice are not restricted to very specialized groups of users, the article has not provided specific information about them, limiting the scope of the analysis to the different ways the hacking practices have been popularized throughout the web and have made knowledge and information more understandable even to non-expert users.
Another limit of the article is the very partial consideration of the historical connections between the modification of MacBook Nano and previous computer hacking phenomena or contemporary forms of modifications of technologies, such as game consoles and smartphones. Clearly, the modification of MacBook Nano is strictly related to other social practices, to the ways in which people adapt and transform other devices, especially their software components, in order to change their aesthetical features or add functions not allowed by the standard commercial configurations.
Although the article has not addressed these implications, it has however showed an example of how hacking culture and practices are becoming more and more common in the experience of today’s average technology users, and how hacking-related objects, competence and discourses are undergoing a process of transformation influenced by cultural codes and discourses belonging to the sphere of market and consumption. This is a particularly interesting phenomenon in contemporary society, where personal technologies, devices and media are becoming increasingly central in the consumer’s experience. In the next few years, we will probably witness a further and even more evident convergence between the original practice of modifying hardware components, typical of the hacker milieu, and the increasing tendency among consumers to modify their own technologies. The case of MacBook Nano here presented can be regarded as a journey into the emerging interactions between hacking and consumption, which – we can reasonably assume – will probably continue to increase in the next few years, becoming an integral part of the ways in which the consumption of digital technologies and services evolves, is appropriated and transformed.
Paolo Magaudda is Postdoctoral Research Fellow in Sociology at the University of Padua, where he works on the social study of science and technology. Besides having published several scientific articles and chapters, in 2011 he has edited (with Federico Neresini) a book in Italian on the representations of science on TV and in 2012 has published his empirical research on the consumption practices of musical technologies. A new book on the representations of science and technology in popular culture is currently in press and is expected by autumn 2012. His website is: www.paomag.net
Works cited
Baldwin, P. (2010), OSx86: Creating an Hackitosh. Indianapolis: Wiley.
Baudrillard, J. (1970) The Consumer Society, Myths and Structures. London: Sage, 1998.
Beer, D. e Burrows, R. (2010) ‘Consumption, Prosumption and Participatory Web Cultures: An introduction’. Journal of Consumer Culture 10(3): 3-12.
Buchanan, M. (2009) ‘The Netbook Hackintosh Video Apple Made Wired Take Down’ http://gizmodo.com/5131264/the-netbook-hackintosh-video-apple-made-wired-take-down 14 January.
Campbell, C. (1987) The Romantic Ethics and the sprtic
Campbell, C. (2005) ‘The Craft Consumer: Culture, craft and consumption in a postmodern society’. Journal of Consumer Culture 5(1): 23-41.
Chen, B.X. (2008) ‘Gadget Lab Video: Running OS X on a Netbook’ http://www.wired.com/gadgetlab/2008/12/gadget-lab-vide/ December 1.
Claburn, T. (2007) ‘Why Run Leopard On A PC? A Hacker Explains’ http://www.informationweek.com/blog/229214735 October 29.
Debord, G. (1967) The society of the spectacle. Detroit: Black and Red, 1970.
Estrada, (2008) ‘MacBook nano Hackintosh’ http://www.maclife.com/article/news/macbook_nano_hackintosh November, 11.
Freiberg, P. Swaine, M. 2000, Fire in the valley : the making of the personal computer, McGraw-Hill, New York.
Himanen. P. (2001) The Hacker Ethic and the Spirit of the Information Age. New York: Random House.
Hine, C. (2000) Virtual Ethnography, London, Sage.
Jordan, T. (2002) Hacking: Digital Media and Technological Determinism. Cambridge: Polity Press.
Jordan, T. (2008) Activism! Direct action, hacktivism and the future of society. London: Reaktion Books.
Jordan, T. Taylor, P.A. (2004) Hacktivism and cyberwars: rebels with a cause?. London: Routledge.
Keizer, G. (2009) ‘Apple Wins Court Victory Over Mac Clone Maker Psystar’, http://www.pcworld.com/article/182218/apple_wins_court_victory_over_mac_clone_maker_psystar.html November 15.
Kozinets, R.V. 1998. ‘On netnography: Initial reflections on consumer research investigations of cyberculture’. Advances in Consumer Research 25(1): 366-72.
Lai, C. (2009) ‘Hackintoshed: Life With My MacBook Nano’ http://gigaom.com/apple/hackintoshed-life-with-my-macbook-nano/ October 8.
Levy, S. (1984) Hackers: Heroes of the Computer Revolution. New York: Doubleday.
Magaudda, P. (2010) ‘Hacking practices and their relevance for consumer studies. The example of the iPhone’s jailbreaking’. Consumers, Commodities Consumption 11(2).
Marx , K. (1847) The poverty of philosophy. New York: Prometeus Books, 1995.
McLean, P. (2008) ‘Steve Jobs on Apple’s cash, NetBooks, Apple TV, and cheap PCs’ http://www.appleinsider.com/articles/08/10/21/steve_jobs_on_apples_cash_netbooks_apple_tv_and_cheap_pcs/ October 21.
Perry, D. (2011) ‘Netbook Market 40% Down – Microsoft’ http://www.tomshardware.com/news/microsoft-q1-earnings-netbook-intel-amd,12677.html May 2.
Reckwitz, A. (2002) ‘Toward a theory of social practices: a development in culturalist theorizing’. European Journal of Social Theory, 5 (2), pp. 243-263.
Ritzer, G. Jurgenson, N. (2010) ‘Production, Consumption, Prosumption: The nature of capitalism in the age of the digital prosumer’. Journal of Consumer Culture 10(1): 13-36.
Rosner D. Bean J. (2009) ‘Learning from IKEA hacking: i’m not one to decoupage a tabletop and call it a day’, Proceedings of CHI 2009: 419-422.
Sassatelli, R. (2007) Consumer Culture. History, Theory, Politics, Sage, London.
Schatzki, T., Knorr Cetina, K. Von Savigny, E. (eds) (2001)The practice turn in contemporary theory. London: Routledge.
Shove E.A., Watson, M., Hand, M. Ingram, J. (2007) The Design of Everyday Life. Oxford: Berg.
Shove, E.A. Pantzar, M. (2005) ‘Consumers, Producers and Practices Understanding the invention and reinvention of Nordic walking’. Journal of Consumer Culture 5: 43-64.
Söderberg J. (2008) Hacking Capitalism: The Free and Open Source Software Movement, London: Routledge.
Taylor, P.A. (1999) Hackers: crime in the digital sublime. London: Routledge.
Teglet, T. (2009) ‘Acer Expects Netbook Market to Reach 30 Million Units in 2009’ http://news.softpedia.com/news/Acer-Expects Netbook-Market-to-Reach-30-Million-Units-in-2009-104841.shtml February 18.
Toffler, A. (1980) The Third Wave, London: Pan.
Turner F. (2008) From Counterculture to Cyberculture: Stewart Brand, the Whole Earth Network, and the Rise of Digital Utopianism. Chicago: University of Chicago Press.
Warde, A. (2005) ‘Consumption and theories of practice’. Journal of Consumer Culture 5(2): 131-153.
Watson, M. Shove, E. (2008) ‘Product, competence, project and practice: DIY and the dynamics of craft consumption’. Journal of Consumer Culture, 8(1), 69-89.
Weber, M. (1921) The protestant ethic and the spirit of capitalism. London: Routledge, 1992
